How the view key solves the privacy vs. compliance dilemma

One of the longest-standing tensions in crypto—and finance as a whole—is between privacy and compliance. Regulators need enough visibility to prevent illicit activity, while users and institutions demand confidentiality, security, and control.
Most systems solve this by collecting and storing sensitive data in centralized databases. It checks the compliance box, but at the cost of security, user trust, and often—regulatory risk.
Aleo flips the model.
Instead of exposing everything by default, every Aleo account comes with cryptographic “windows” that stay sealed unless the user opens them. These are view keys—protocol-native tools for selective disclosure, built directly into the account model.
In this article, we’ll go deep on what the view key is, how it works, and why it’s the missing piece for building private, compliant dapps.
You don’t have to choose between privacy and compliance
Accounts on Aleo come with built-in cryptographic “windows” that stay sealed unless the account owner opens them. These are the view keys — protocol-native tools that give read-only visibility without compromising security or control.
Imagine your Aleo account is a locked diary. The private key lets you write and control what’s inside. But instead of exposing all data by default, every account comes with built‑in cryptographic “windows” that can be opened only when the owner says so. Those windows are the view keys.
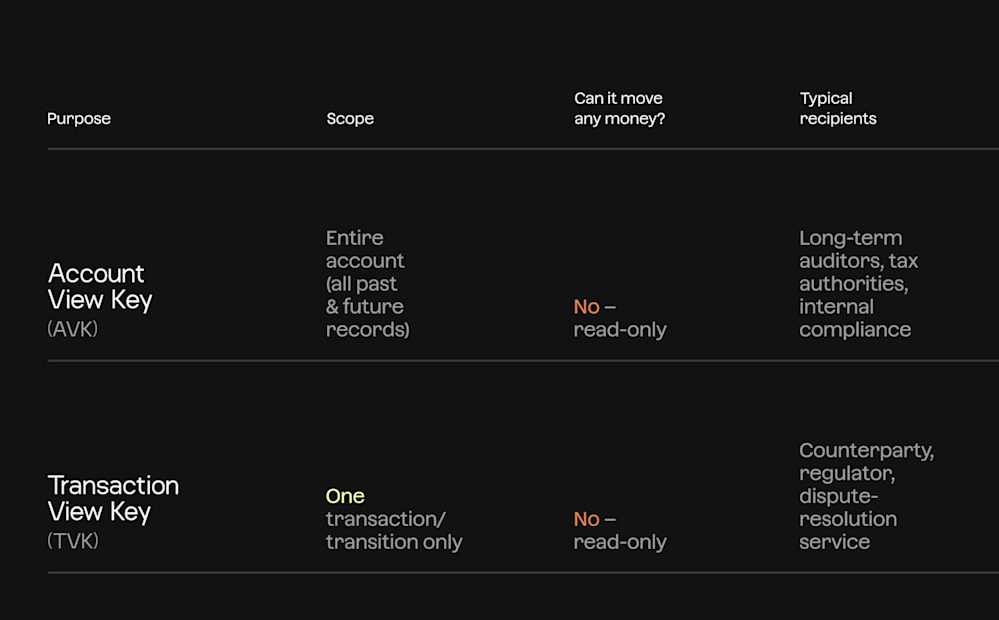
There are two levels of visibility: account view keys and transaction view keys.
This architecture gives Aleo a significant edge in the push for regulated, privacy-preserving crypto systems.
Selective transparency: Meet AML/KYC “on request” clauses without storing sensitive data in plaintext.
Least-privilege access: Share only what’s necessary—reducing GDPR exposure and minimizing breach risk.
On-chain verifiability: Because the TVK hash is recorded on-chain, auditors can verify that no data has been tampered with or forged.
These features aren’t just regulatory niceties—they unlock entire categories of apps that were previously impossible to build on-chain without sacrificing security or user trust.
Types of view keys
Aleo’s view key system actually includes two distinct layers of visibility: the Account View Key and the Transaction View Key, each designed to provide a different level of disclosure.
Account View Key (AVK)
Think of your Aleo account as a personal journal. You write in it every time you make a transaction. The private key is the pen—you need it to write new entries, and it must stay secret.
Now imagine you want someone (a bank, tax authority, or compliance officer) to read your journal—not edit it, just read it. That’s where the Account View Key (AVK) comes in.
The AVK is derived from a user’s private key. When shared, it gives the recipient full visibility into all encrypted records tied to that account—past and future—while preserving spend security.
The AVK is a read-only key that reveals everything about your account’s activity without ever exposing your private key or granting spend access. It’s cryptographically derived from your private key, but impossible to reverse engineer. So even if someone has the AVK, they can't touch your funds.
Use it when:
You need to undergo an audit
You want to prove you’re compliant
A regulator needs visibility across your full account
Transaction View Key (TVK)
Sometimes, you don’t want to share your whole journal—just one page. Maybe you're settling a dispute, validating a single payment, or working with a compliance officer on a specific event.
The Transaction View Key (TVK) is built for exactly that. Every time you send a transaction on Aleo, your wallet automatically creates a unique TVK for that transaction. This key decrypts the private inputs and outputs of just that one action—nothing before it, nothing after.
Even better, it’s tamper proof: the hash of the key gets committed to the blockchain as part of the transaction, so anyone you share it with can verify its authenticity.
Use it when:
You want to share proof of a specific transaction
A counterparty needs to verify private details
You want pinpointed transparency without overexposing yourself.
Aleo’s view key model enables least-privilege transparency, where data is disclosed on a need-to-know basis—securely, and with cryptographic audit trails. To understand how this selective disclosure works in practice, let's examine the building blocks that make it possible.
Conclusion
This isn’t privacy as an add-on. It’s privacy and compliance, by design.
The view‑key architecture gives everyone a clean separation of duties:
Customers stay in full control of disclosure.
Developers build dApps that default to privacy yet remain audit‑ready. (without sacrificing compliance)
Institutions & regulators receive cryptographically verifiable data only when policy requires it.
In short, Aleo’s view keys remove the false choice between regulatory compliance and user privacy, unlocking an entire class of financial applications that were previously impossible to deploy on public blockchains.