What is a Merkle tree?

In the world of cryptography, few data structures are as fundamental as the Merkle tree. Named for computer scientist Ralph Merkle, who first described them in the late 1970s, these binary tree structures serve as the backbone for secure, efficient data verification across distributed systems. From Bitcoin's transaction validation to modern zero-knowledge proof systems, Merkle trees provide the cryptographic foundation that makes trustless verification possible.
This article will walk you through how Merkle trees work, why they're essential for blockchain security, and how they power the privacy-preserving applications built on Aleo.
How do Merkle trees work?
Think of a Merkle tree like a family tree, but instead of tracking relatives, it tracks pieces of data. Each "leaf" contains a hash of some information, which is similar to a digital fingerprint. Moving up the tree, each parent node contains a combined hash of its children. At the very top sits one master hash that represents everything below it.
Here's how it works: imagine you have four documents—A, B, C, and D. Each document gets its own unique hash. Then you combine hashes A+B to create a new hash, and C+D to create another. Finally, you combine those two to create the root at the top.
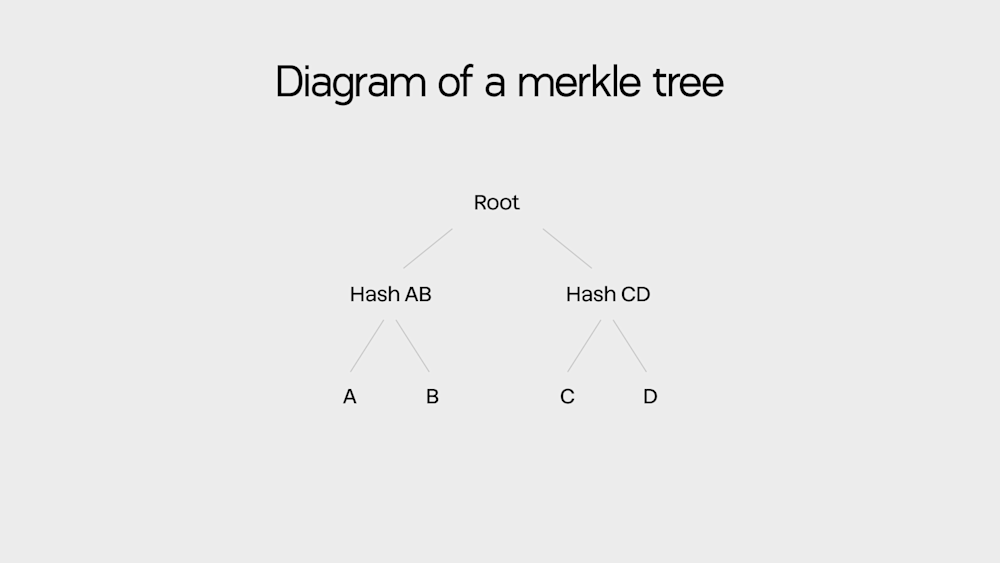
This design is brilliant because changing even one letter in document A creates a completely different hash for that document (assuming collision resistant hash function is used). This new hash then changes the combined hash above it, which changes the master hash at the top. The entire tree acts like a tamper-proof seal for digital information.
How Merkle trees make verification simple
Here's where Merkle trees get really clever. Let's say you want to prove that document A is part of your collection, but you don't want to share all four documents with someone.
With a Merkle tree, you only need three things:
Document A itself
Hash B (A's sibling)
Hash CD (the other branch)
The person verifying can then:
Create a Hash of document A
Combine it with hash B to recreate hash AB
Combine hash AB with hash CD to recreate the root
Check if this matches the root
Think of it like proving you're enrolled at a school without viewing the entire student database. You need your student ID, your homeroom roster, and your grade level summary. The principal can verify you belong by checking: your ID matches the homeroom list, your homeroom is part of the grade level, and your grade level exists in the school.
This process is incredibly efficient. Even with millions of documents, you only need about 20-30 hashes to prove any single document belongs—not the other 999,999+ documents. It's like finding a specific book in a library by checking just a few shelf labels instead of every single book.
How Merkle trees solve blockchain’s biggest problem
Blockchains face a massive challenge: how do you let people verify transactions without forcing them to download enormous amounts of data? For context, Bitcoin's blockchain is over 500GB and growing daily. Downloading all that data would make blockchain verification impossible for most devices.
Merkle trees solve this perfectly. In Bitcoin, every block contains thousands of transactions that are all stored on the blockchain, but instead of including all transaction details in the block header, Bitcoin stores just one Merkle root. This creates three major benefits:
Instant Fraud Detection
If someone tries to fake a transaction, the master hash won't match what everyone expects, immediately exposing the fraud. The entire network can detect tampering without examining every individual transaction.
Lightweight Verification
Mobile wallets can verify payments without downloading entire blocks. Your phone only needs the block headers (about 80 bytes each) plus a small Merkle proof, making Bitcoin accessible on smartphones and tablets.
Efficient Storage
The network saves enormous amounts of bandwidth by sharing hashes instead of bulky transaction data. A proof that used to require downloading thousands of transactions now needs just a few hashes.
Aleo takes this efficiency even further by combining Merkle trees with zero-knowledge proofs, so you can verify transactions while keeping all the details completely private.
How Merkle trees enable selective disclosure
Modern privacy systems use Merkle trees in creative ways beyond simple verification. They enable something called "selective disclosure"—proving specific facts about your data without revealing the data itself.
For example, imagine a digital age verification system. Instead of showing your full birth certificate to prove you're over 21, you could use a zero-knowledge proof system. Your age verification could be cryptographically proven without revealing your exact age, birth date, or any other personal information - you'd simply demonstrate that you meet the age requirement. A Merkle tree might be used as part of this system to efficiently verify that your age data is included in a trusted dataset, but the range proof itself would require additional cryptographic techniques beyond what Merkle trees provide natively.
Projects like Aleo combine Merkle trees with zero-knowledge proofs to create applications where privacy and verification work hand-in-hand. Users can prove facts about their data without revealing the data itself, opening up possibilities we're just beginning to explore in areas like private stablecoins, identity verification, NFTs, and more.
The future of Merkle trees
As technology advances toward better privacy and security, Merkle trees are evolving too. They're becoming key components in quantum-resistant security systems—the digital protection of tomorrow that even quantum computers can't break.
One exciting development is sparse Merkle trees, which assign a slot to every possible piece of data (even empty ones). This allows for "non-membership proofs"—proving that something doesn't exist without revealing what you're looking for. For instance, you could prove you've never been convicted of a crime without revealing all of the information in a background check.
Conclusion
Merkle trees are the invisible infrastructure that makes secure, private applications possible. Whether you're building private voting systems, confidential financial apps, or secure identity platforms, Aleo provides the tools to implement Merkle tree verification while maintaining complete privacy.
Ready to build the future of privacy-preserving applications? Start exploring Aleo's developer documentation.


